Building VPC, EC2 on Console in AWS
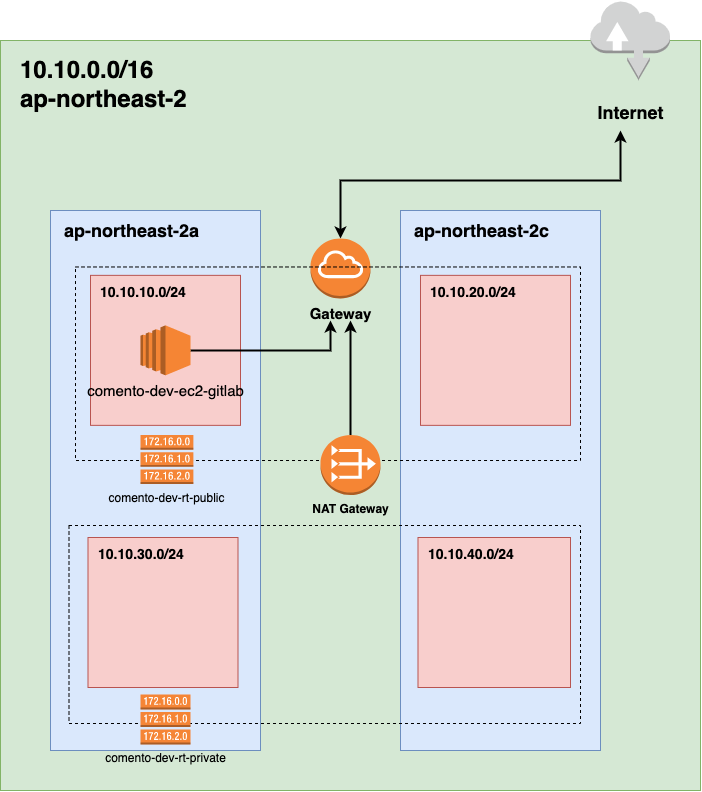
Table of contents
Region
click national name text right and top of the window

Select Region name on the list(Ex> Asia Paciffic(Seoul) ap-northeast-2)

VPC
Overview
This topology’s concept is HA(high-available). VPC was built as 10.10.0.0/24 on the ap-northeast-2(Seoul) region. And it was divided from 10.10.10.0/24 to 10.10.40.0/24 into 4 subnets. 2 subnets(10.10.10.0, 10.10.20.0) was selected to ‘ap-northeast-2a’ and ‘ap-northeast-2c’ each other as the public subnet. Also, the other 2 subnets were selected to ‘ap-northeast-2a’ and ‘ap-northeast-2c’ each other as the private subnet. the public route includes 2 public subnets with an internet gateway. the private route includes 2 private with a nat gateway.
VPCs
Type ‘VPC’ in Serach blank box. and click ‘VPC’ on the list.

Your VPCs > Create VPC

Select ‘VPC only’ under ‘Resources to create’ and put VPC’s name you want into blank box under ‘Name tag’(ex> dev-pj-vpc)

Put IPv4 CIDR as B Class into blank box under ‘IPv4 CIDR’ and let rest of options as defualt, click ‘Creat VPC’ after done.

Check VPC’s name, status, IPv4 CIDR you made on the VPCs list.

Subnets
Click ‘Creat subnet’ after clicking ‘Subnets’ on the VPC’s sidebar.

Select VPC you made before by selecting the box under ‘VPC ID’.

Put the subnet name you want into the blank box under the Subnet name; for example, dev-pub-a-sub.

Select the Availability zone where this subnet will reside within the region you selected; for example, ap-northeast-2.

Put the subnet’s IPv4 CIDR block into blank box under ‘IPv4 CIDR block’. block sizes must be between a /16 netmask and /28 netmask; for example, 10.0.0.0/24.

Click ‘Add new subnet’ after done.
Make 3 more subnets following below the list as needed from this 01.PROJECT.
Subnet name Availabilty zone IPv4 CIDR dev-pub-c-sub ap-northeast-2c 10.10.20.0/24 dev-pri-a-sub ap-northeast-2a 10.10.30.0/24 dev-pri-c-sub ap-northeast-2c 10.10.40.0/24 Click ‘Create subnet’ after done.
Check system message at top of window and Subnets information(Name, Status, IPv4 CIDR)you made on the list.

Internet Gateway
- An internet gateway is a VPC component that enables communication between your VPC and the internet. To use an internet gateway, attach it to your VPC and specify it as a target in your subnet route table.
Click ‘Creat internet gateway’ in the internat gateway section after clicking ‘Internet gateways on ther VPS’s left sidebar

Put internet gateway name into blank box under ‘Name tag’;for example, dev-igw. and click ‘create internet gateway’.

Check the message ‘The following internet gateway was created [internet gateway ID, name] you can now attach to a VPC to enable the VPC to communicate withe internet.’ on the top of the window. so, click ‘Attach to a VPC’ on the right of message.

Select VPC you made just before on the box under ‘Available VPCs’ in ‘Atttach to VPC section’ and click ‘Attach Internet gateway’.

Check the message ‘Internet gateway [internet gateway ID] successfully attached to [VPC ID] on the top of the window.

Nat Gateway
You can use a network address translation (NAT) gateway to enable instances in a private subnet to connect to services outside your VPC but prevent such external services from initiating a connection with those instances.
A public NAT gateway enables instances in private subnets to connect to the internet but prevents them from receiving unsolicited inbound connections from the internet. You should associate an elastic IP address with a public NAT gateway and attach an internet gateway to the VPC containing it.
Click ‘Create NAT gateway’ in ‘NAT gateways’ section after clicking ‘NAT gateways’ on the VPC’s sidebar.

Put NAT gateway name into blank box under ‘Name - optional’;for example, dev-ngw.

As you know, NAT gateway have to communicate with out side internet. so, It should be created on public subnet and get public IPv4 address. for this reason, select one of public subnet in the selecting box under ‘Subnet’.

Select ‘Public’ in 2 options under ‘Connectivity’ couse you can recive ‘Elastic’ IP only when you select ‘Public’. and click ‘Allocate Elastic IP’ after done.

Check the message ‘Elastic IP address xxx.xxx.xxx.xxx on the top of the window. and check ‘Elastic IP allocation ID’ that was allocated middle of window.

Click ‘Create NAT gateway’ after done.

Check the message ‘NAT gateway [NAT gateway ID]|[NAT gateway name] was create successfully on the top of the window. and check details information. Make sure keep seeing state until it turn from pedding to available and then, check ‘Primary public IPv4 address’, ‘Primary private IPv4 address’.

Route Table
A route table refers to a table that consists of a set of rules, called routes, that are used to determine where network traffic is directed. In AWS, each subnet in a Virtual Private Cloud (VPC) is associated with a route table, which controls the traffic routing for the subnet. The routes in a route table determine where traffic is directed, either to an Internet gateway, virtual private gateway, Elastic IP address, a VPC endpoint, or another VPC in the same account.
Each VPC has a default route table that controls the traffic routing for all of its subnets. In addition to the default route table, you can create additional custom route tables, which can be associated with one or more subnets in your VPC. This allows you to specify different routing rules for different subnets in your VPC.
Click ‘Create route table’ on the route tables section after clicking ‘Route tables’ on the VPS left sidebar.

Make sure, It needs 2 different route tables in this 01.PROJECT. one is a public route table that can communicate with the Internet, and one other is a private route table that It can’t communicate from outside the internet.
First of all, put ‘route table’s name’ for the public route table’s name into the blank box under ‘name - optional’; for example, dev-pub-rt.

Select the VPC you made just before on the box under ‘VPC’.

Click ‘Create route table’ after letting ‘Tags’ as default.

Click ‘Edit routes’ under the detail tab ‘Routes’ after checking the message ‘Route table [route table ID]|[route table name] was created successfully’.

Click ‘Add route’ on the left down at the Edit route section to add rule in this route table.

At New ‘Edit routes’ was expaneded from ‘Edit routes’, put 0.0.0.0/0 into into blank box under destination. that means ‘the target IP or IP range requested from this route table’.

Select ‘Internet gateway’ on the selecting box under ‘Target’. and than, It is writ ‘igw-…’ into box, show igw ID you made just before on the list.

It shows ‘igw-…’ on the box with ‘igw ID’ you made just before on the list. Click your ‘internet gateway ID’ on the list. and then, click ‘save changes’.

Check ‘Edit subnet associations’ in one of Tap; ‘subnet associations’ under ‘Detail’ information box. after checking the message ‘Update for route for [route ID]/[route table name] on the top of the window.

Select 2 public subnets on the ‘Available subnets’ list because this is for the public route table. and then, click ‘Save associations’ after done.

Check the message ‘You have successfully updated subnet associations for [route table ID]/[route table name]’ on the top of the window. so now we made a public route table that any resource on the public subnets in this route table can communicate with outside internet. also, It can connect to public subnets from outside the internet.

Click ‘Create route table’ in ‘Route tables’ section again. from now, you’ll make a private route table. it can request from private subnets to outside internet through NAT gateway but, It can’t connect from Outside internet to private subnets.

Set information in ‘Create table’ section as the following next chart.
| Create route table | |
|---|---|
| Name - optional | VPC |
| dev-pri-tb | dev-vpc |
| Edit route | |
|---|---|
| Destination | Target |
| 0.0.0.0/0 | dev-ngw |
| Edit subnet association | |
|---|---|
| Available subnets | dev-pri-a-sub |
| dev-pri-c-sub |
EC2
Amazon Elastic Compute Cloud (Amazon EC2) is a web service that provides scalable computing capacity in the Amazon Web Services (AWS) cloud.
With this, you can launch and manage virtual servers (called instances) in the AWS cloud. Also, you have complete control over the instances you launch and can configure them to meet your needs. EC2 allows you to scale your computing resources up or down, as needed, by adding or removing instances.
Instances are assigned a unique public IP address and can also be assigned a public DNS name, making it easy to connect to them from the Internet.
You can use this to run a wide range of applications and services, including web applications, databases, analytics tools, and big data processing pipelines. These also support a variety of operating systems, so you can run the software you need for your application.